With the new release v5.2.0, the open source workflow engine Imixs-Workflow now supports the asynchronous execution of BPMN events.
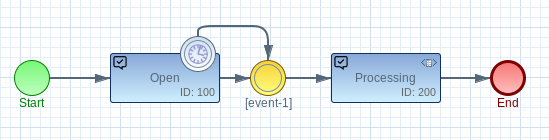
This feature is a big step forward especially in a microservice architecture. The new so called AsyncEvents make it much more easier to decouple a Rest API call from the processing life cycle of the workflow engine. In this way the request-response pattern shows better performance and allows a very clear design of complex business processes.
The AsyncEvents were already part of the Imixs-Microservice project in a pre-release and become now a core feature of the Imixs-Workflow engine. Especially in more complex architectures, the use of the so-called SAGA Pattern is an important building block. With asynchronous events Imixs-Workflow is now supporting this design pattern as a core feature. Read also our blog about building powerful microservice solutions with the SAGA Pattern.

 With the next minor release 4.3. of
With the next minor release 4.3. of 